With COVID-19 forcing businesses around the globe to shift to remote work, the cybersecurity landscape has changed significantly.
Consequently, the complexity of protecting corporate infrastructure grew tenfold. It is complicated enough to instate impenetrable protection and incident response lifecycle when all the company employees work from the office — but it becomes a nightmare when working remotely.
However, it seems that working from home is here to stay even after the lockdowns get lifted. Thus, businesses ought to prepare to live in the new reality of ensuring cybersecurity for environments with vast surfaces susceptible to attack. In order to do this, they should dynamically secure and track multiple external endpoints and connections.
However, this situation is old news for seasoned cybersecurity professionals. They simply add more routine checks to a cyber incident response plan in place in their companies and continue working as usual. But what do you do if you don’t have a security incident response plan yet?
Read on to learn what that plan is, what are the stages of the incident response life cycle from NIST, as well as how to properly implement it.
First of all, why do we talk about a cycle here? Cybersecurity professionals know that it is not a question of WHETHER a data leak, system security breach, or service shutdown will happen — it is a question of WHEN. Realizing you need an incident response program in the middle of an incident is a rude awakening for any business.
Therefore, a good practice is to prepare in advance by instating incident response procedures, performing red-blue training exercises, fake data breaches, and penetration testing. Your team must go through the workflows and look for intrusions as actual incidents occur. Adjusting the incident response process has to be based on both findings of the training and the outcomes of actual accidents.
NIST (the National Institute of Standards and Technology) is the largest and most trusted provider of standards and procedures for the IT industry. It maintains and constantly updates a huge database of known code vulnerabilities, viruses, and other cybersecurity threats, as well as develops procedures for discovering and remediating them.
This way, your incident management lifecycle is being constantly revised and updated using the latest findings in order to keep your team on the same page and timely react to new threats.
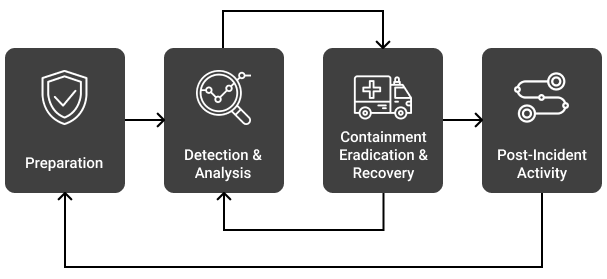
Let’s get a detailed breakdown of what is happening at each stage.
A well-documented incident response plan with clear step-by-step instructions for handling an incident will help your team avoid making critical mistakes in the case of attack.
The reader should have a step-by-step guide for handling an incident, with flowcharts and checklists.
Incidents of low or medium severity don’t require the same focus or resources as those considered to be critical to the mission. Thus, your team should be able to identify the incident severity and handle it by the playbook.
If the team identifies a high-priority threat, they should have clear instructions on how and when to escalate the information to appropriate stakeholders to form a proper incident response unit.
Every business stakeholder must be fully aware of their roles during handling an incident. The incident response plan must include relevant people from other departments, not only the core IT team. For instance, the PR must make a statement, and marketing might need to pause the campaigns while the systems are shut down; HRs should inform the employees, legal must deal with the possible consequences, etc.
Preparing on-point guidelines for handling repetitive low- and medium-priority incidents will help reduce the toil significantly. Forming a general incident response process flow for dealing with major cybersecurity threats and service disruptions requires a clear understanding of the goals.
Your company has to remain as operational as possible even during the worst cybersecurity incidents. Workflow continuity, crisis management, and recovery plans must also be in place and interconnected to enable seamless handling of the situation as well as prevent obstruction of the business.
One of the key factors contributing to the success of this stage is the complete buy-in of the cybersecurity initiatives from the managerial body, as money spent on security is never wasted — they help contain the security breach when it does happen and prevent financial losses and reputational fiascos for your business.
According to the recent IBM report on cybersecurity, the average period of system
breach detection in 2019 was 206 days, and it took 73 more days on average to contain and remediate the threat. This means that, if there is no security incident response program in place, hackers can have nearly a year of access to your systems and data before you can really do anything about it.
These are the essential components of incident detection and analysis:
Monitoring the activity of your users and devices within your network is essential for building a solid cybersecurity protection. However, most of the controls like corporate firewalls or Intrusion Detection Systems are now hamstrung, as with the lockdowns the centralized corporate infrastructure protection and monitoring systems became non-effective.
Modern antivirus and monitoring systems harness the power of behavioral big data analytics to discover infected devices when they connect to the corporate network. This helps safeguard your digital assets and fill the cybersecurity gap created by the rise of remote office connections.
If your systems are already compromised (remember, it might take almost a year before you can notice it), your system access credentials and business-critical information might be already available for sale on the dark web. Cybersecurity experts can monitor this market to inform you if such a threat arises and prepare ways to remediate it.
Alerting is also an essential component of timely incident response procedures. This helps identify malicious activity quickly, stem the panic, and reduce the time before the containment and mitigation of the attack.
Should they wait for confirmation of each action from their superiors, valuable time
could be lost and the malicious breach might succeed. However, if every team member does what they want and the stakeholders aren’t informed about what is being done — the result would be chaotic and potentially disastrous.
This is why it is important to have an ingrained muscle memory and clear incident response workflow understanding from multiple attack simulations. It helps the team keep a cool head under pressure and avoid making critical mistakes.
Clearly defined communication channels and reporting procedures will keep the management in the loop of the situation, so they make informed decisions. It will also allow them to issue commands without majorly disrupting the efforts of the cybersecurity team that deals with containing and eradicating the threat.
You should also gather feedback from all stakeholders and incorporate the results of
the incident analysis in the post-mortem. This way, your organization will come out of the storm stronger than before and will be able to handle future potential incidents better.
It can also be quite useful to employ the services of external incident response forensics. Having resolved a multitude of incidents in various market sectors and industries, they will provide invaluable insights on the way your team handled the incident and possible improvements of the process. This will help strengthen your response to incidents in the future and adapt your cyber incident response plan accordingly.
Now you should have gotten a solid understanding of the stages of the incident response lifecycle, the reasons to have it, and the best practices for designing and implementing your cybersecurity incident response program.
Should your company lack access to the required expertise — UnderDefense is here to help you.
We can evaluate your cybersecurity profile and provide recommendations on how to minimize your potential attack surface and tighten your cybersecurity measures.
Speak to a cybersecurity expert today to safeguard your business!